On November 21st, Ukraine’s Computer Emergency Response Team (CERT-UA) was alerted to a new string of ransomware attacks, strongly indicated to be the work of a Russian state-aligned advanced persistent threat dubbed Sandworm.
Bratislava-based cybersecurity firm, ESET, analyzed the attacks and identified them as part of new ransomware strain that they named RansomBoggs.
As of the time of this writing, the extent of the attack and its effectiveness are unclear, but recent Russian tactics, and previous efforts by the cyber criminals in Sandworm indicate that Ukrainian power grids are a likely target.
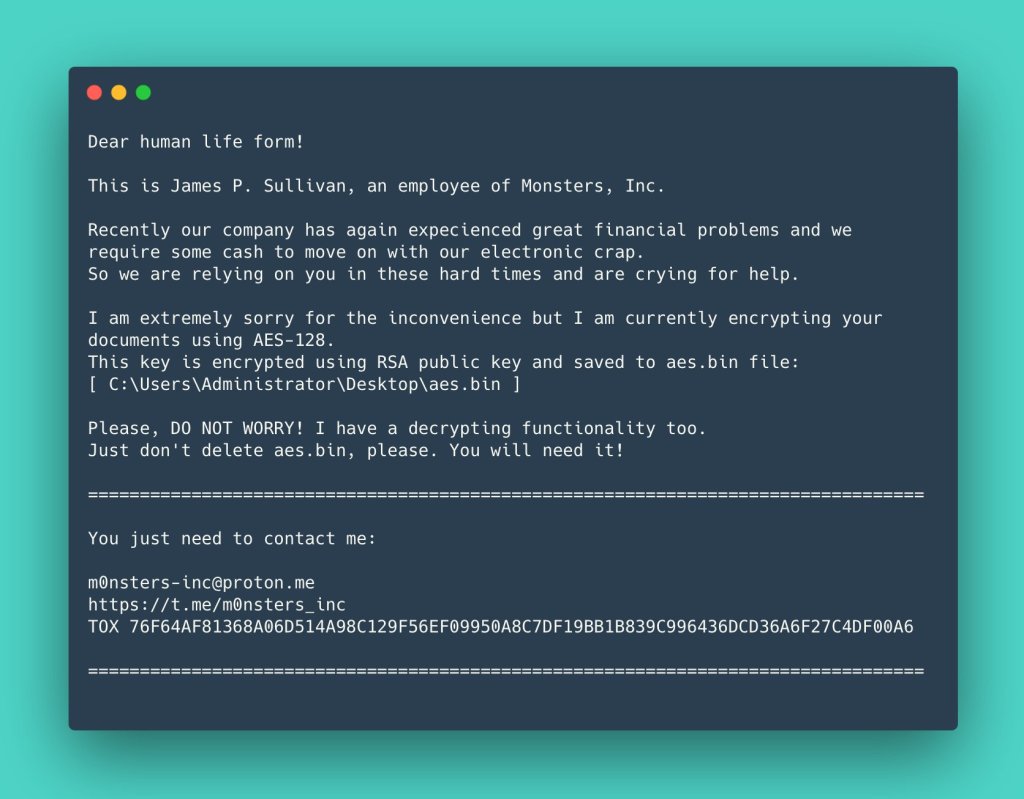
The ransomware appears new and has been written in .NET, but its method of deployment is what prompted ESET to attribute the malware to Sandworm. The smoking gun was a Powershell script used to deploy the malware baring a striking resemblance to one used during the Industroyer2 attacks earlier in the invasion. Industroyer2 was attributed to Sandworm, and targeted Ukraine’s energy sector.
ESET tweeted a brief explanation on November 25th:

